designed for small businesses
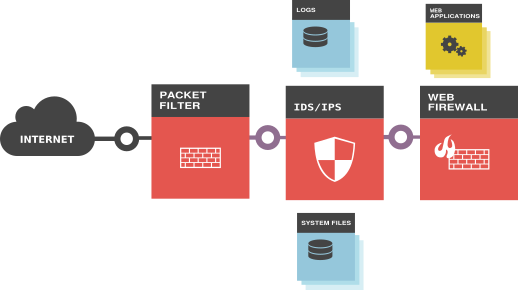
We help small businesses with the system and network security solutions. Commercial tools today are either complicated to operate or prohibitively expensive to install for the majority of small businesses. We aim to change that. Our primary product is a software package that targets security in four critical areas in an online business:
- Dynamic packet filtering
- Intrusion Detection
- System file baselining
- Web application firewall
Superior usability and value
Easy to use
Misconfiguration is among the top 5 reasons why websites are exploited. Configuring a secure server requires in-depth knowledge of the operating system and the network stack. This process can be intimidating for the small businesses. We keep your server secure so that you can focus on your business.
Cloud-Ready
AwareOS is packaged in Deb file format that is an established software distribution mechanism in Debian and Ubuntu Linux environments. Our products are used in all three major cloud service providers and other co-located VPS environments.
Affordable
With flexible monthly subscription plans and no long-term commitment, you can fit network security into your budget however you like. Our plans scale as your needs evolve. In fact, we are so confident that all our plans come with a 2-week free trial period.